The US Department of Justice has taken down a cryptocurrency hacking group. What does this mean?
The US Department of Justice has reported a successful operation against the Hive hacker group, which engaged in extortion and used cryptocurrencies for this purpose. The operation lasted several months, in cooperation with the US FBI, and yielded good results – the Department reported that it had “dismantled” an entire network of cybercriminals. We report on the situation and its role for the decentralised asset industry.

We already know of examples of such hacker activity. In particular, in the summer of 2020, they blocked the system of the University of California, a group of researchers from which was studying COVID-19. In the end, during lengthy discussions, the hackers did achieve a payout of 116 bitcoins.
Importantly, 2022 proved less profitable for cryptocurrency ransomware hackers. According to Chainalysis analysts, the fraudsters earned the equivalent of $457 million during this period, while 2020 and 2021 were far more profitable.
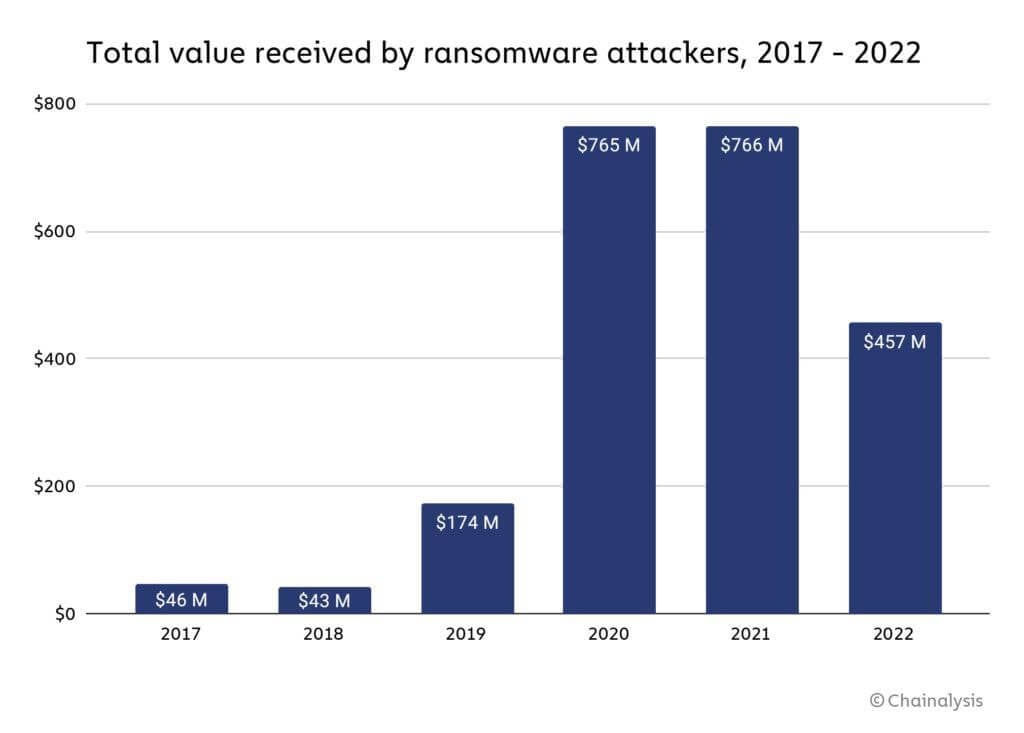
Hackers’ earnings for cryptocurrency extortion
As experts point out, such a trend could be due to a trivial reluctance to pay ransoms to victims. Accordingly, this creates a certain inconvenience for hackers.
How cryptocurrency hackers are being dealt with
US Attorney General Merrick Garland has declared the operation a success this week. Here’s a pertinent rejoinder.
Last night the Justice Department dismantled an international network of hackers responsible for extorting and stealing hundreds of millions of dollars from victims in the US and around the world.
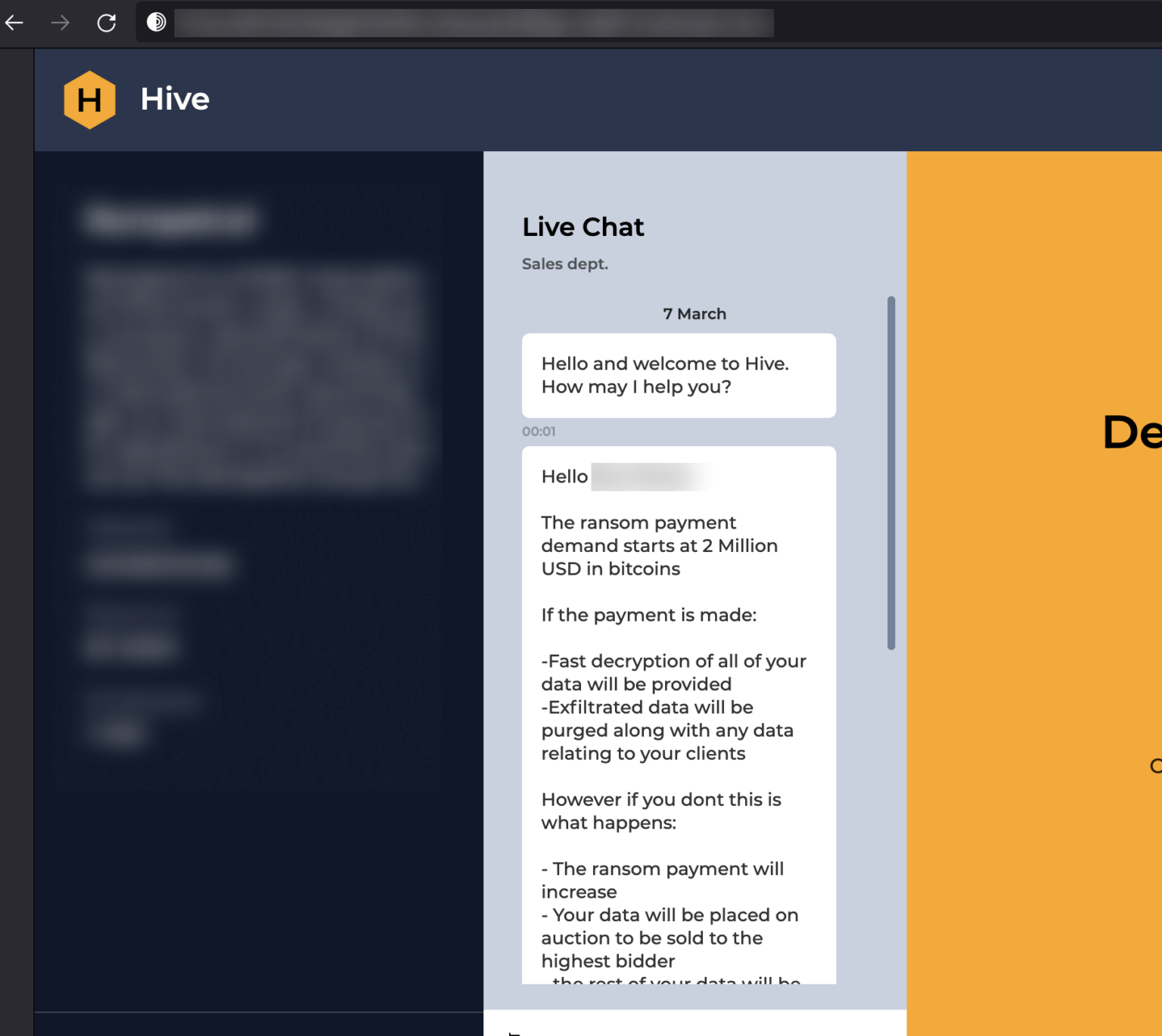
Hive ransom demand
Sources say the group has attacked more than 1,500 victims worldwide since June 2021 and received more than $100 million in crypto ransom payments. The FBI’s overall operation to infiltrate the Hive network began in July 2022. Intelligence agencies were able to obtain more than 1,300 decryption keys to help victims recover their data and systems, including critical infrastructure.
As a reminder, such hackers first rely on blocking data on the victim's devices. They then contact the victim and offer to provide the decryption key for a fee. The ransom is often asked to be paid in cryptocurrencies. The most experienced hackers use privacy-focused coins like Monero, which support so-called shielded transactions.
According to Decrypt, Hive’s attack vector is based on stealing sensitive data such as emails, documents, photos and videos, and then encrypting it. The hackers then demanded a ransom in Bitcoin for the decryption key needed to recover the files. In addition, more money was extorted from victims in exchange for a promise not to publish the stolen data on the darknet. If the victim did not pay, Hive would publish or sell the information obtained, which could lead to further problems.

Cryptocurrency hacker
Fighting cybercrime has long been an important priority for the crypto industry. The day before, the developer of the eponymous cryptocurrency wallet Phantom detailed the problem of phishing attacks in its blog. It should be recalled that during such attacks scammers are trying to steal the victim’s confidential data by tricking them. Phantom announced that its wallet has scanned more than 85 million transactions and blocked more than 18 thousand of them malicious.
It should be noted that most often users receive a warning when they try to conduct a transaction with an address that is involved in various violations of the law. Also in some cases, companies are prevented from making the corresponding transfers. And while this may sound like a restriction on users' freedoms, in fact, newcomers are helped by such initiatives as follows - without even realising it.
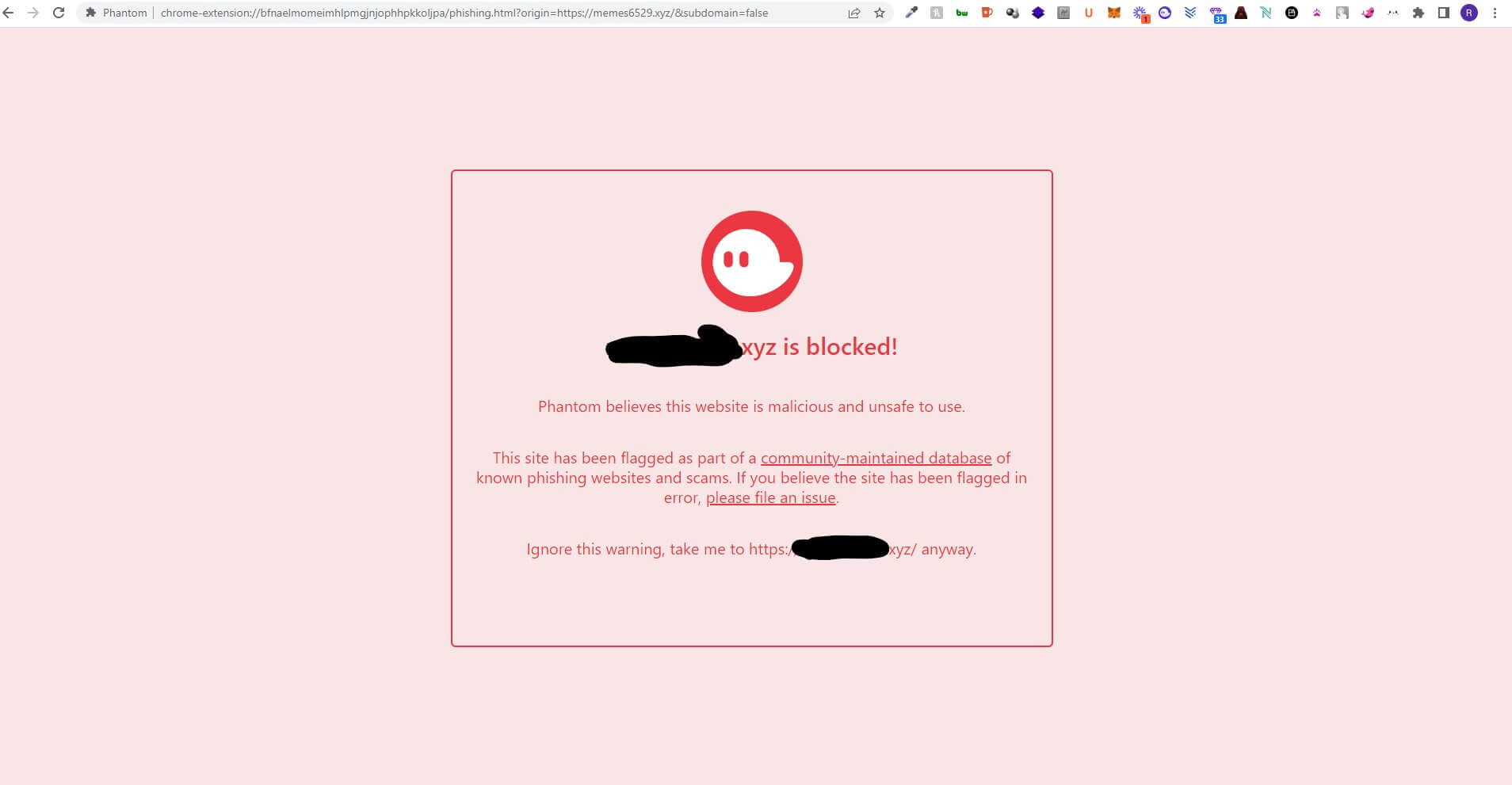
Blocking a suspicious site with Phantom Wallet
Phantom has also helped thousands of users avoid falling into the trap of hackers: the wallet blocks suspicious sites that have malicious code and could lead to loss of funds. This was a real revelation for some users – one of them shared on Twitter that Phantom had prevented him from visiting one of the malicious sites, Decrypt reports.
Note that we've previously looked at the Phantom wallet's capabilities. Read more about its settings in a separate article.
Phantom Wallet
We believe that such news will positively influence reputation of crypto-assets. After all, for people unfamiliar with the field of coins, it means increased security, as well as the ability of law enforcement to get to law-breakers. Accordingly, crypto is not a far cry from the "Wild West" that this niche is often fondly referred to as.















