Top 5 new phishing attacks by cryptocurrency scammers. What are they like and how to counter them?
The SlowMist platform recorded a total of 303 blockchain security incidents in 2022. Of those, 31.6 percent involved phishing, a type of fraud that aims to gain access to sensitive data, such as passwords or private keys, by deceiving the victim. In a recent report, analysts highlighted five of the most popular phishing methods last year, which we’ll discuss. Here are the details about them.
It should be noted that some variants of the scam promise a rather low chance of success, but scammers still use them. For example, a similar scheme was recently warned about by representatives of Ledger, a company that manufactures hardware wallets.
In short, scammers send small amounts of coins to random addresses. In this way, they hope that an inattentive user will see such a transaction among the last ones in the wallet in use, take this transfer as theirs, and then send cryptocurrency there. Naturally, this would only work if the user was planning to transfer funds to one of his wallets beforehand. If he uses the address for long-term storage, getting crypto-assets from a potential victim will definitely not work.

Ledger’s latest generation of hardware wallets called Stax
These aren’t the only popular fraud schemes for 2022. Here they are.
Contents
- 1 Malicious browser bookmarks
- 2 Free NFTs
- 3 Trojan with malicious code
- 4 Transaction signature
- 5 Similar address attack
Malicious browser bookmarks
This approach involves injecting malicious code into the bookmark manager, an extension or portal available to Internet browsers. SlowMist gave an example of an incident where fraudsters could gain access to a cryptoproject creator’s account. Here’s their quote.
By inserting JavaScript code into bookmarks through these phishing pages, attackers could potentially gain access to user information in Discord.
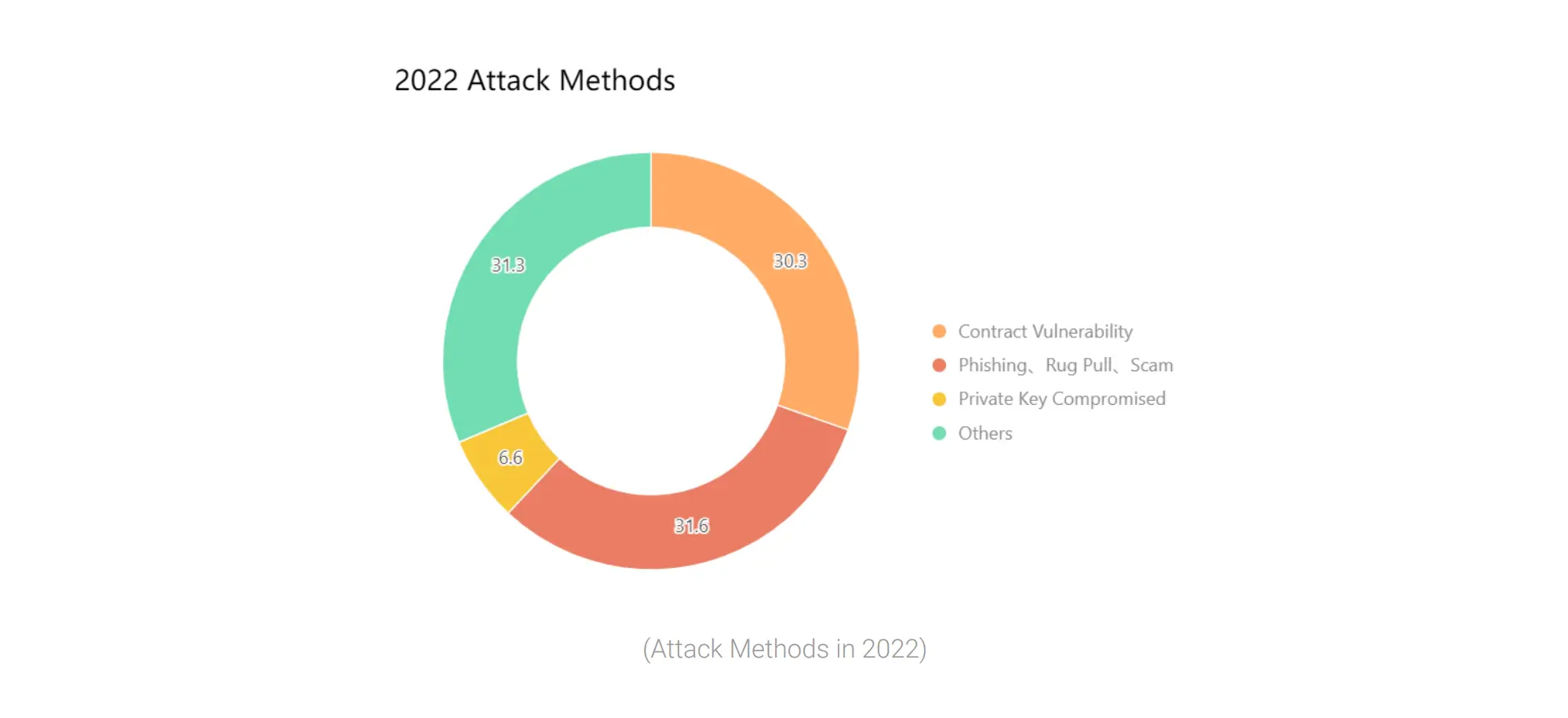
The most popular methods of phishing attacks
After directing a victim to add a malicious bookmark via a phishing page, the attacker waits for the victim to click on the bookmark and log into Discord. This triggers the embedded JavaScript and sends the victim’s personal information to the scammer’s Discord channel.
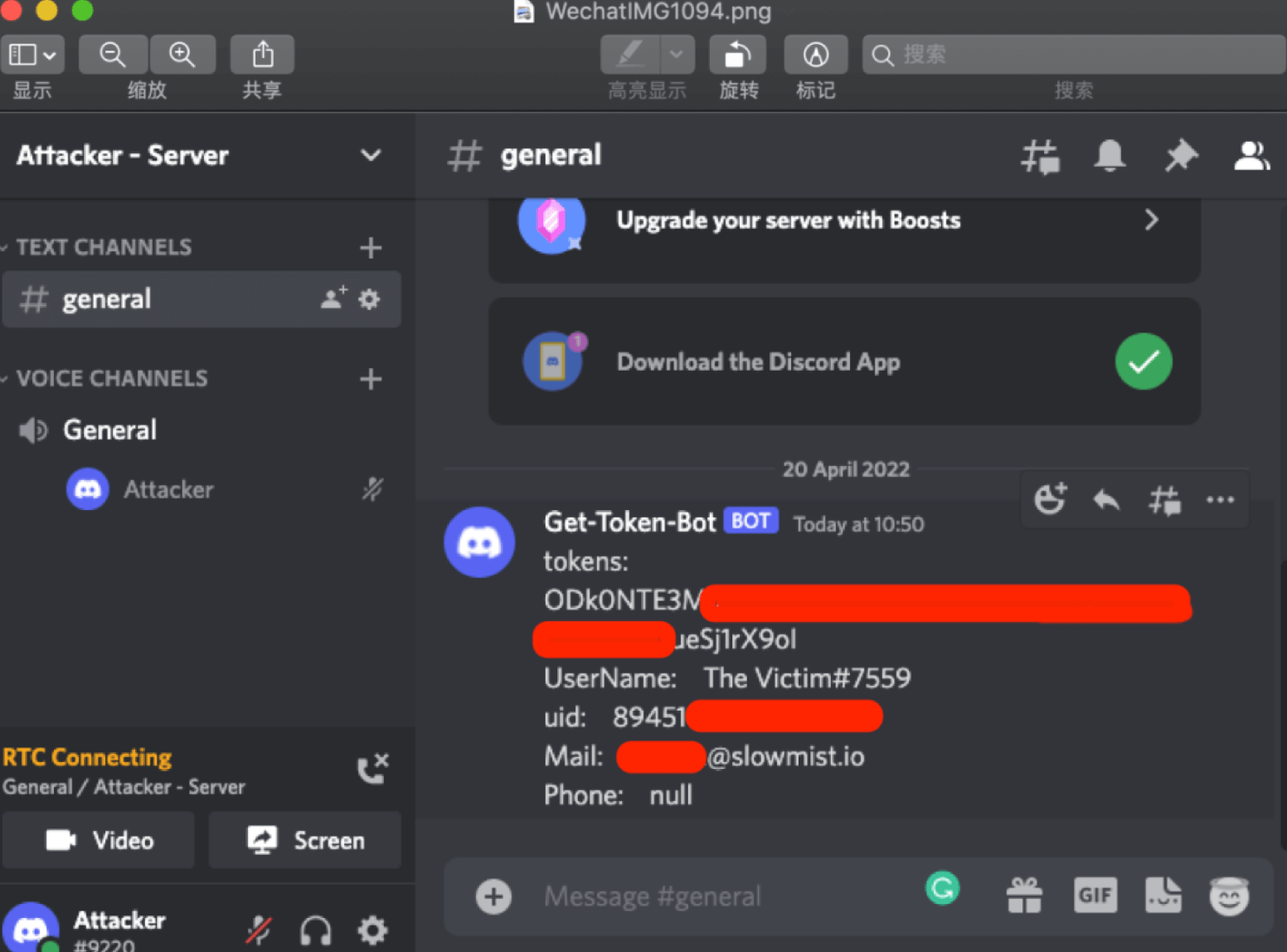
The victim’s token
During this process, a fraudster can steal the victim's token in the form of an encrypted username and password and thus gain access to her account. This, in turn, would allow them to post fake messages and links to other phishing websites, posing as the victim. And as we know, scammers in Discord are quite successful at stealing expensive NFTs.
Here again, it is important not to upload unnecessary files from unverified sources. They may contain viruses.
Free NFTs
Out of 56 fraudulent incidents involving unique tokens, 22 cases were the result of phishing. The scam with supposedly free NFTs is that the victim is redirected to a fake website, where they are asked to sign a smart contract interaction to receive a token for 0 ETH or other cryptocurrency.
The fraudster can then use the signature to purchase the victim’s other NFTs on trading platforms for his or her own price. The transaction is free of charge on the part of the buyer, meaning that the victim simply loses their unique tokens, which are sent to the scammer’s wallet.
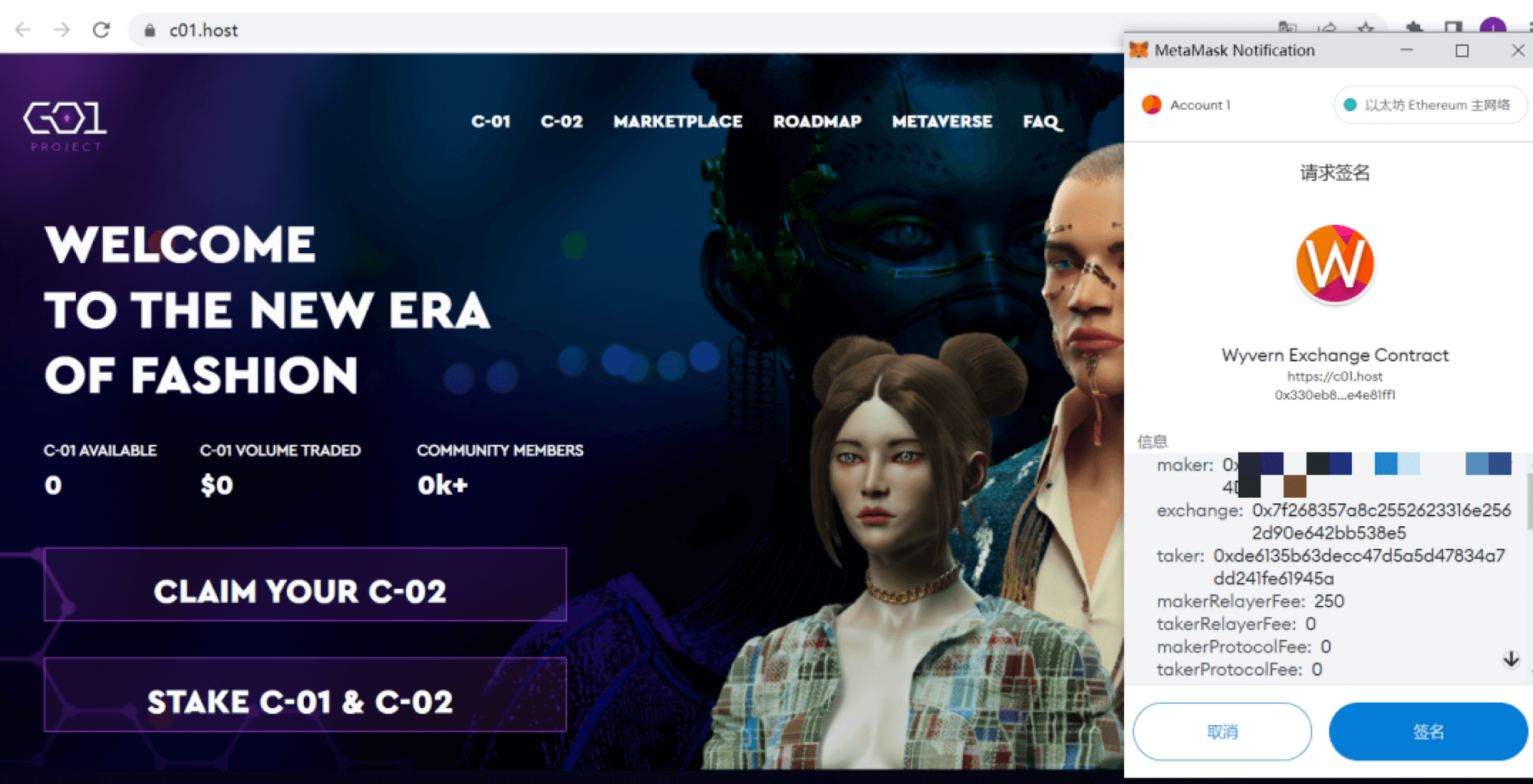
Signature offer in Ethereum
To combat this method of cheating, SlowMist recommends cancelling all active NFT bids on trading platforms like OpenSea. In addition, do not sign any smart contracts unless it is a popular official project.
Trojan with malicious code
According to Cointelegraph’s sources, this phishing attack method is usually carried out via private messages on Discord, where the attacker invites victims to take part in testing a new project. He then sends the program in the form of an archive containing an executable file of about 800 MB. Once the program is downloaded, it scans files containing key phrases like “wallet” and uploads them to the attacker’s server. Here’s an expert quote on the subject.
The latest version of RedLine Stealer also has the ability to steal cryptocurrency by scanning information about an installed wallet on a computer and uploading it to a remotely controlled machine.
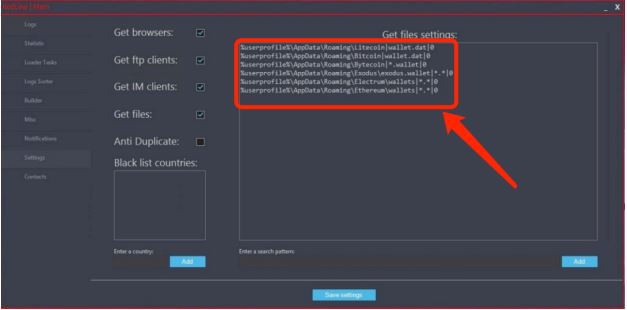
Trojan
Such a Trojan can periodically perform various actions on an infected computer, scan it for other secret combinations, or execute commands from a remote location on the attacker’s machine. A protection against this phishing technique is not to download suspicious files from the Internet.
Transaction Signing
This phishing attack allows the attacker to use the victim’s private key to sign any transaction they want. The key can be obtained by directing the victim to a fake site offering any reward they wish, as long as they sign the transaction.
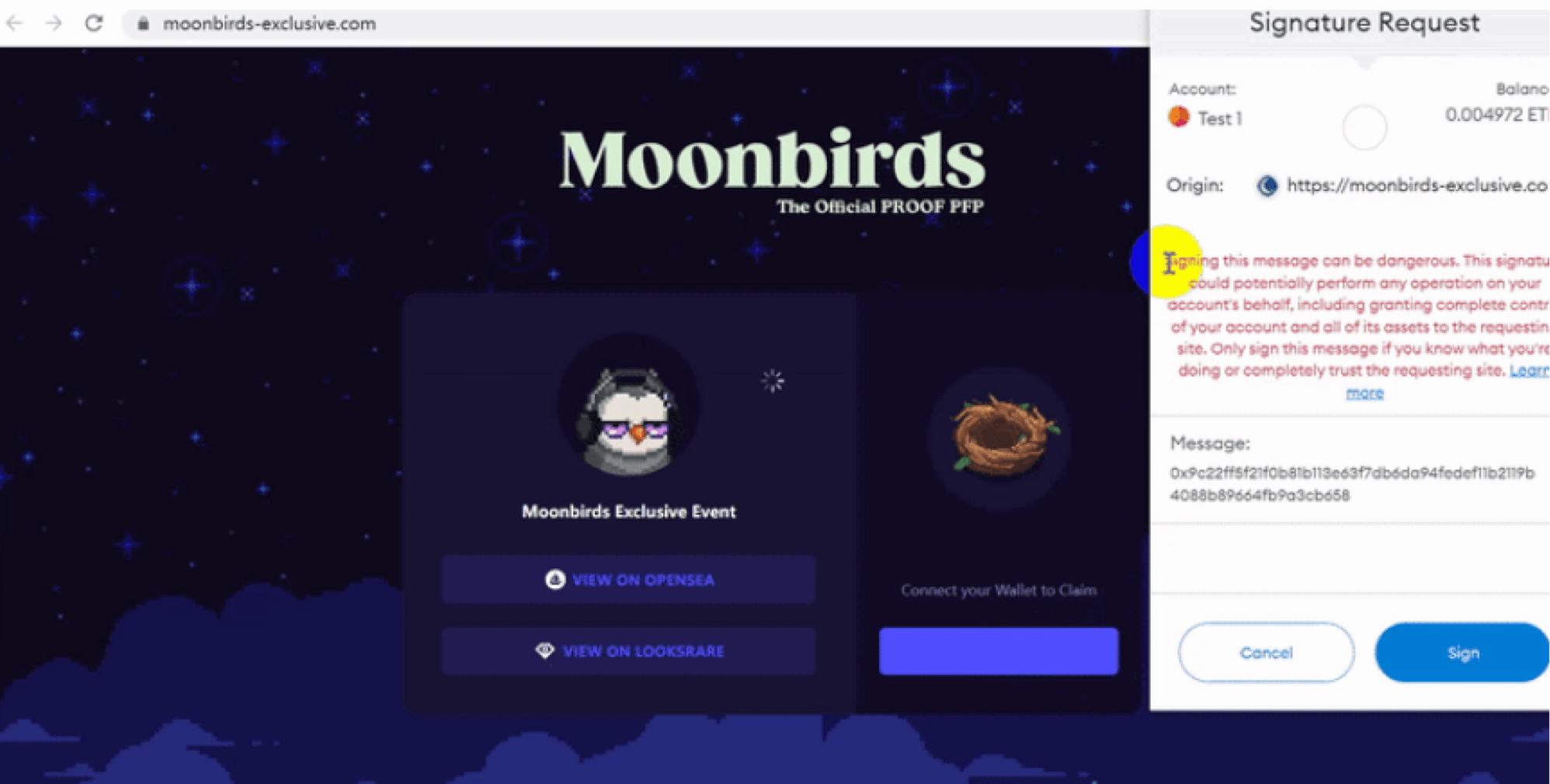
Signing the transaction
Once signed, attackers can conduct remote transactions with the victim's address, such as transferring tokens or accessing a smart contract. Remember, sign any blockchain interactions only after they have been thoroughly verified. If verification fails, it is safer to ignore the offer or opportunity.
Attacking similar addresses
This is probably one of the most interesting tactics of attackers. They send small pieces of cryptocurrency – for example, 0.01 USDT – to wallets whose address differs from their own by only the last couple of characters. The calculation is based on user’s inattention: he can accidentally send the coins to the scammer’s wallet instead of his own, copying it from transaction history.
Here is a screenshot of a victim of such an attack. Note that the ending of two different addresses is the same, but the beginning is different.
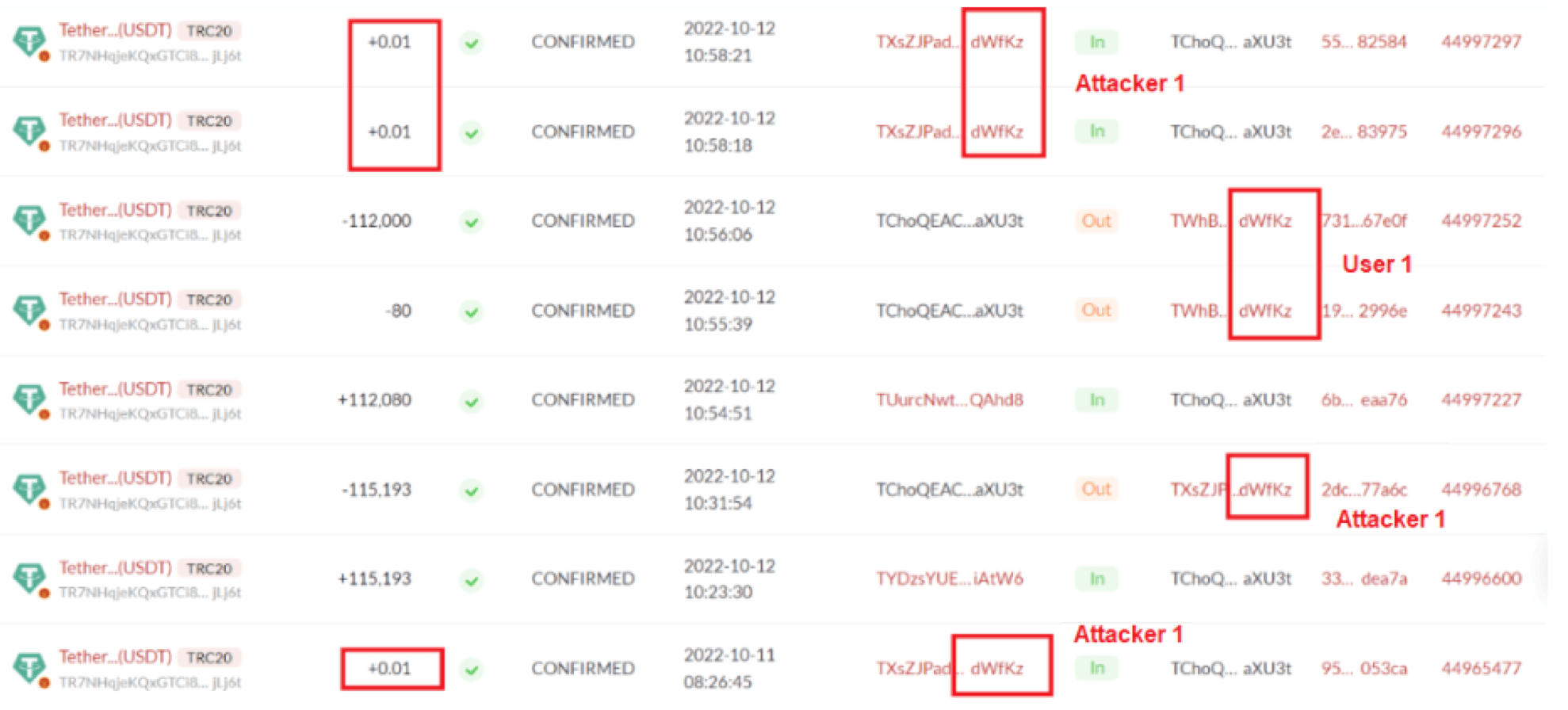
Transactions to similar addresses
Both the more sophisticated and simpler phishing methods are easily defeated. A user just needs to follow basic cybersecurity rules and be attentive. And if a user has just started interacting with cryptocurrencies, it is better to buy a hardware wallet and ignore any complicated blockchain interactions like non-obvious smart contract signatures to trigger NFT. As one becomes more familiar with the world of decentralised assets, the nature of a particular action will become clearer, and the list of possible user steps will also become broader.
You can read about other interesting things in our Millionaire Crypto Chat. There we will discuss other important developments affecting the blockchain world.















