Hackers are stealing crypto from Android users with a new stealthy programme. How does it work?
Experts from cybersecurity company McAfee have discovered a new malicious Android client called SpyAgent. It is able to steal private keys from screenshots and photos stored on a smartphone. More specifically, the malware uses an optical character recognition (OCR) mechanism. With its help, it scans the images on the smartphone and extracts words from them that allow you to get to other people’s coins and empty victims’ wallets.

The main target of hackers in the world of cryptocurrencies is cid-phrases or so-called mnemonic phrases of users. These are unique combinations of 12, 18 or 24 words that are generated when setting up non-custodial wallets like Phantom, Ledger, MetaMask and others.
They act as a master key to manage different addresses in the networks of different cryptocurrencies. With this in mind, stealing a syd allows you to get to the contents of all the victim’s wallets created within this combination.
Therefore, when interacting with different cryptocurrency wallets, this phrase should be fixed on a piece of paper, which will then be stored in a safe place.

Sid-phrase and cryptocurrency wallet
The peculiarity of the cid-phrase is that anyone with access to it can manage coins on linked addresses and send them to themselves. That’s why the topic of recovery phrase security essentially means the safety of the coins themselves.
How do you not lose your cryptocurrencies?
McAfee Labs representatives explained that the malware spreads through links sent in text messages. To infect a device, it is enough for an unsuspecting user to click on the received link and perform a number of actions.

Cryptocurrency hacker
It redirects the victim to a website offering to download an app. However, this app has SpyAgent in its code – installing it will lead to data compromise on the phone.
Hence, the first important conclusion is that users should ignore any links sent by strangers. The consequences of clicking on them can be very unpredictable, so it is safer to skip any such offers.
The second valuable recommendation is not to take photos or screenshots of such combinations. Still, any internet-enabled device like smartphones can be remotely hacked. Thus hackers are able to get to other people's coins and create a lot of problems for their victims. So you should only write your sids on physical media like paper or special metal plates.
.
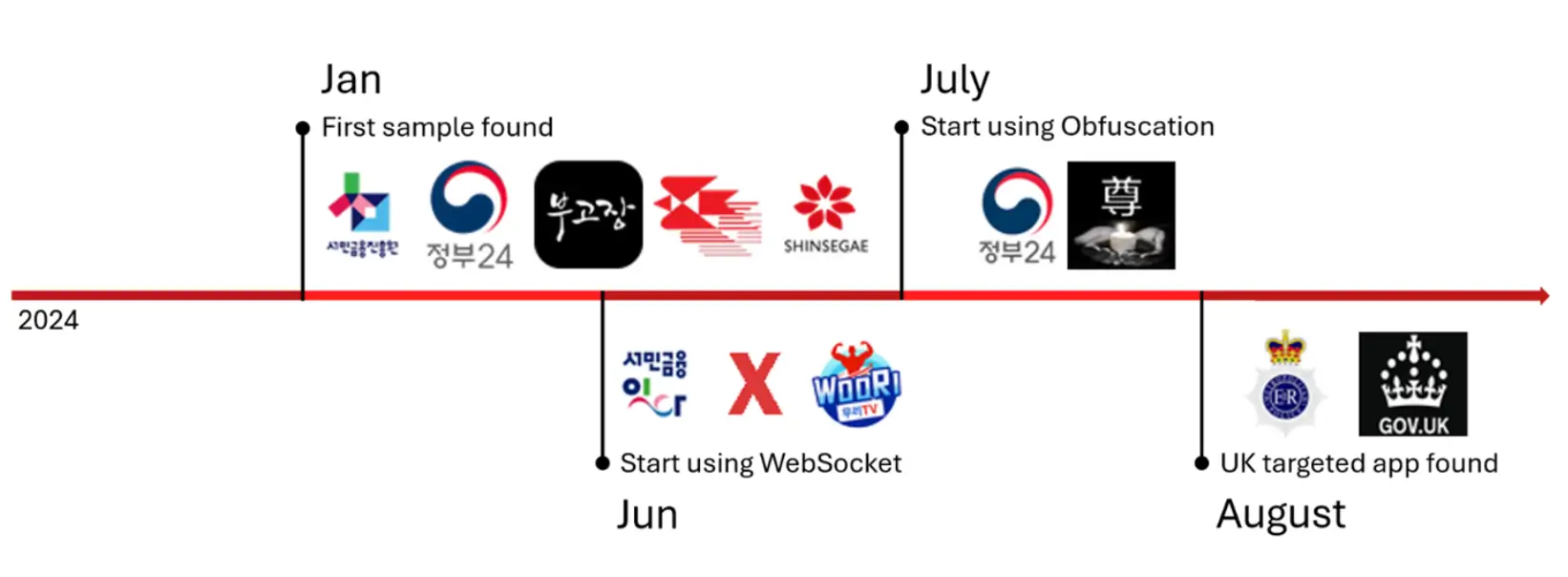
Malicious applications found by McAfee
According to Cointelegraph’s sources, SpyAgent masquerades as banking and government apps, as well as streaming services. When installing the apps, users are prompted to give it permission to access contacts, messages and local storage.
So far, SpyAgent is mainly targeting South Korean users, although McAfee experts have already detected malicious code in more than 280 fake apps. Unfortunately, this is just another problem in a long list of threats from hackers.
A similar malware targeting macOS systems called Cthulhu Stealer was discovered in August. Like SpyAgent, Cthulhu Stealer masquerades as an ordinary app and steals user’s personal information, including MetaMask passwords, IP addresses and private keys for cryptocurrency wallets.
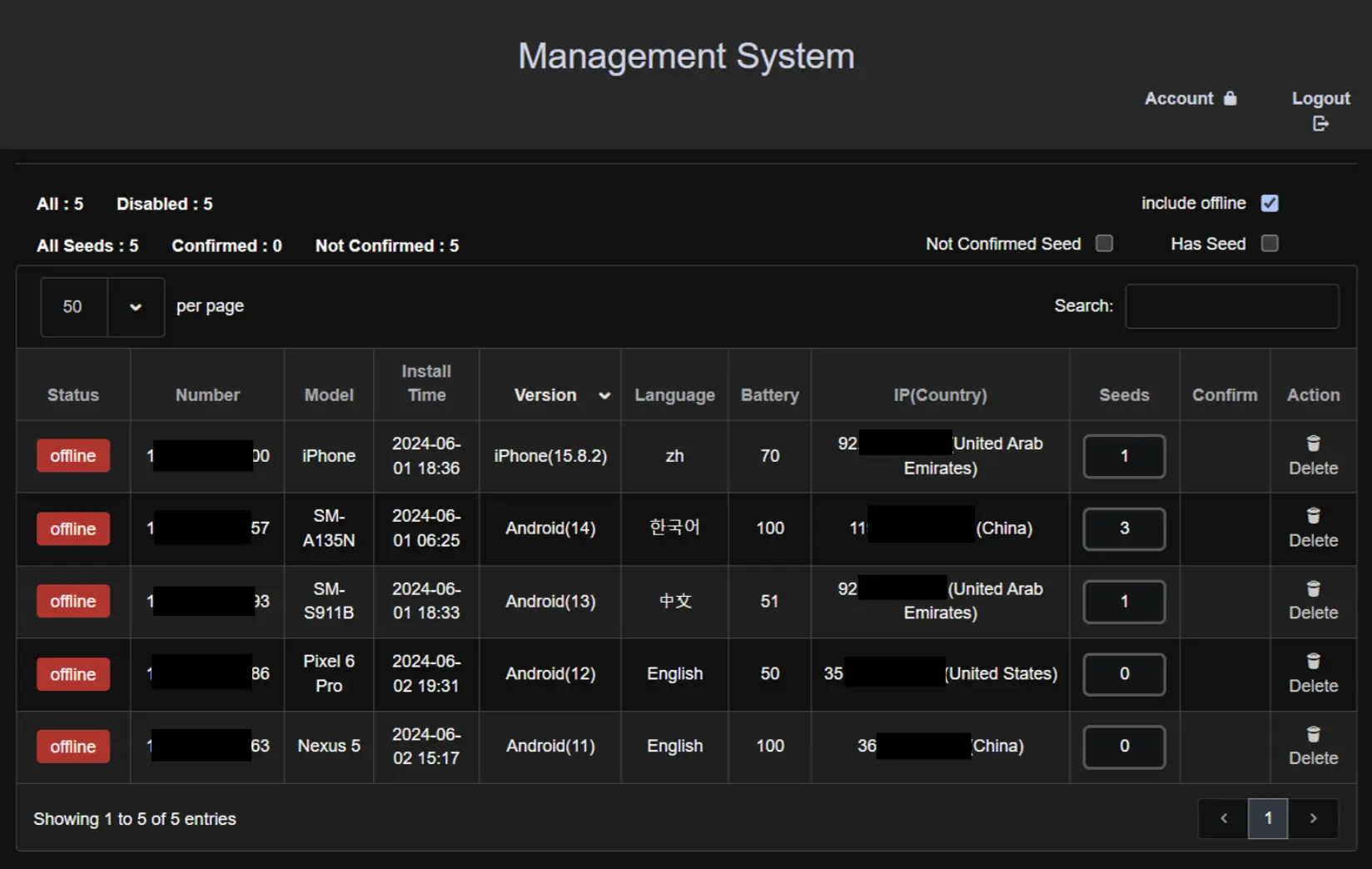
A platform for managing data stolen by hackers
In the same month, Microsoft discovered a vulnerability in Google’s Chrome web browser that could have been exploited by a North Korean hacker group called Citrine Sleet. Basically, the hackers created fake crypto exchanges and used these sites to send out job applications to unsuspecting users.
The victim who followed this process inadvertently installed remotely controlled malware on their system, which stole their private keys.
Fortunately, law enforcement agencies around the world are making successful moves to combat attackers. In one landmark case in Scotland, £110,000 in crypto was confiscated from 29-year-old John Ross Rennie. This is the first time that proceeds of crime legislation has been used to confiscate crypto as physical cash, CryptoPotato reports.
The case was heard at the High Court in Edinburgh, with Rennie being found guilty of possession of stolen goods following a robbery in Blantyre in March 2020. On that day, three men broke into a house and forced the victim to transfer 23.5 BTC into their wallet.
During the attack, the woman inside the house was beaten several times and thrown into a bedroom. The attackers then fled.
Cryptocurrency thieves
Although Rennie denies involvement in the robbery, he was named by law enforcement as the “technical brains” of the operation, as he handled all crypto transactions during the heist. Despite his role, Rennie received a relatively lenient sentence of 150 hours of unpaid work and a six-month supervision order.
On 3 September, the defendant’s lawyers at the High Court in Edinburgh agreed that the bitcoins confiscated from him could be converted into cash.
Hackers will always be present in the cryptocurrency industry as this area is extremely lucrative for them. Therefore, it is easier for coin holders to accept this fact and make every effort to protect their own capital. In particular, you should use a hardware wallet, which should ideally be used exclusively for sending and receiving coins. Sid should be kept in a safe place on paper, well, and any links and offers to earn money on the Internet is safer to ignore. Then the chances of saving the crypto and waiting for the end of the bullrun will increase significantly.















