Apple has recognised a critical vulnerability in the company’s devices that allows crypto theft. How to protect yourself?
Users of “apple” equipment need to pay attention to the security of their cryptocurrency wallets. On the eve of the representatives of the technology giant Apple announced the discovery of a vulnerability of devices, opening access to hackers to the digital assets of victims. In general, Apple’s system was threatened by an exploit that allows remote execution of malicious code via the web using JavaScript. Accordingly, crypto holders should take care not to fall prey to fraudulent activity.

At times, Apple’s technology can help find lost cryptocurrency, and in serious amounts. This happened to Chris Janczewski, an IRS agent, who used a MacBook Pro. Thanks to the device, the employee was able to track down and subsequently confiscate about 120 thousand bitcoins.

The laptop used in the search for bitcoins stolen from Bitfinex
They were stolen from crypto exchange Bitfinex in 2016. At the time of the hack, the amount was valued at $67.47 million, but the digital assets are now worth more than $11 billion.
Read more about the history and whereabouts of that very device in a separate piece.
Vulnerabilities in Apple hardware
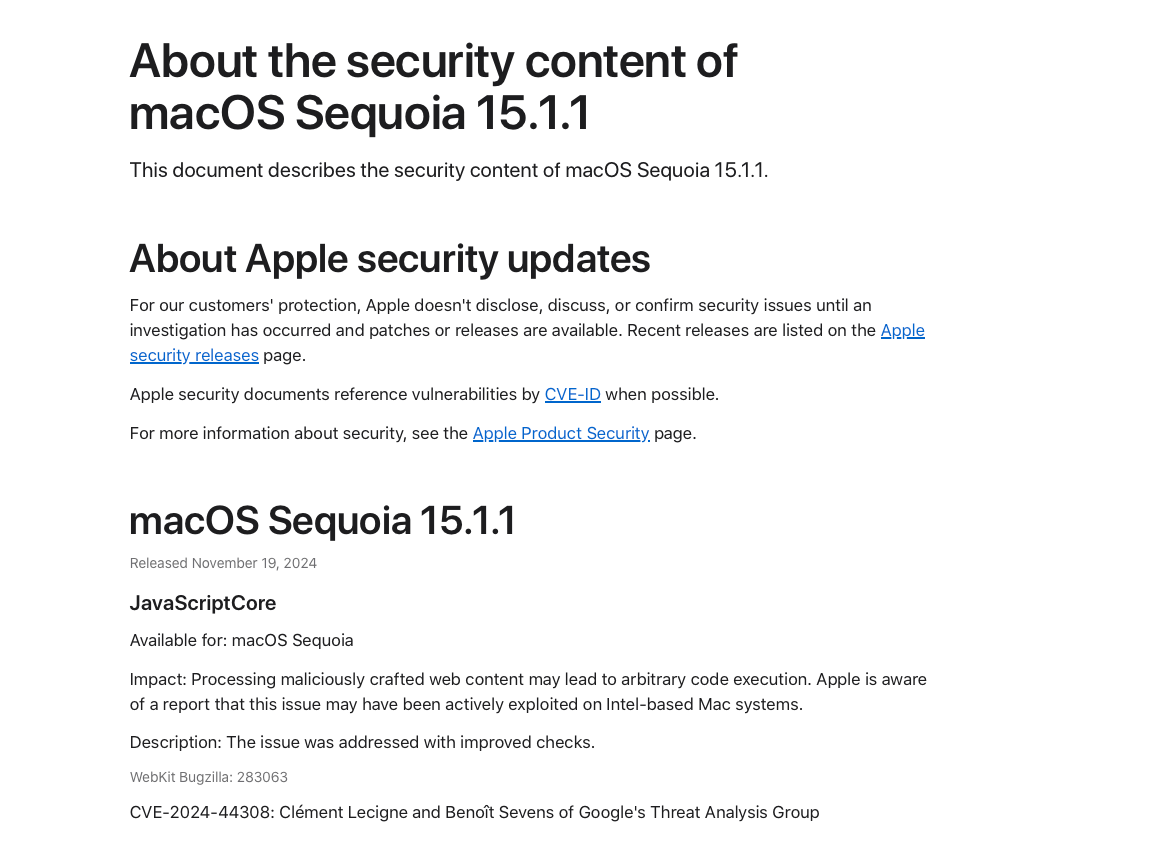
Users of old software can become potential victims of malicious attacks. According to Decrypt sources, users are advised to immediately update JavaScriptCore and WebKit to the latest versions to eliminate the vulnerability. It is noteworthy that initially the bug and the hole in the code were found by researchers from Google.
Apple’s warning about the vulnerability
In addition, Apple acknowledged that it is “aware of active exploitation” of the vulnerability on Mac devices with Intel processors. A similar warning was also issued for iPhone and iPad owners.
The JavaScriptCore vulnerability could allow arbitrary code execution when visiting malicious websites. A software update should fix the issue, the company emphasised.

MacBook Pro
According to Trugard CTO and co-founder Jeremiah O’Connor, attackers could have gained access to sensitive data like private keys or passwords stored in the browser. This could lead to the theft of cryptocurrencies if users’ devices were left without updates.
This situation highlights the weakness of so-called hot wallets. They run inside a browser or as a separate app on a device and store encrypted private keys.
The key vulnerability of such solutions is that they are always connected to the internet, allowing hackers to get to them. Therefore, investors should traditionally only store with such solutions the amounts they need for transactions.
Rumours about the potential threat to users have already started to circulate actively in the crypto community. In particular, the former head of the world’s largest crypto exchange Binance Changpeng Zhao in his Twitter published a corresponding warning about what is happening.
If you’re using a MacBook with an Intel chip, upgrade to the latest software version immediately!
Unfortunately, this isn’t the only problem with Apple’s tech. Back in March, it became clear that devices based on the company’s M1, M2, and M3 series processors could be at risk of hacker attacks.
Recall that the transition to them became an important step in the development of the company’s hardware lines, and the new products themselves allowed to significantly increase the performance of laptops and desktops while improving their autonomy.

Apple iPhone 16 Pro
The vulnerability allows hackers to steal keys to cryptocurrency wallets. It exploits the “prefetching” or prefetching process used in M-series processors to speed up devices. Malicious code can store sensitive data in the processor’s cache and then use it to recover keys that should be inaccessible.
Unfortunately, this security hole persists at the hardware level, meaning it cannot be fixed with software updates. The only possible solution is to implement workarounds that sacrifice performance for security.
😈 MORE INTERESTING STUFF CAN BE FOUND IN OUR YANDEX.ZEN!
It’s important for cryptocurrency wallet owners to remember that the security of their assets largely depends on themselves. In the case of centralised platforms, it is mandatory to connect two-factor authentication (2FA) to protect access to the account. This will minimise the likelihood of unauthorised access to coins and their subsequent withdrawal.
Storage of private keys must be proper. In particular, never share them with third parties or save them in publicly accessible places like cloud storage or text files on devices. It’s best to write down your keys on paper and keep the sheet in a safe place.
Updating your wallet software is another important aspect. Manufacturers regularly release updates that fix vulnerabilities. Neglecting them can leave your wallet vulnerable to attacks.

Ledger Stax hardware wallet
Most crypto assets should be held on hardware wallets, which should ideally be used solely for sending and receiving coins. Hot wallets can be used for day-to-day transactions, but the amounts on them should be minimal.
The current situation is a reminder that internet-connected devices cannot be considered ideal for storing digital assets. Still, they can fall victim not only to hackers, but also to serious bugs. Therefore, it is definitely not a good idea to store all crypto on hot wallets.
.
You can find even more interesting things in our crypto chat room. Be sure to check it out to keep up to date with the situation inside the coin industry and the course of the current bullrun.
SUBSCRIBE TO OUR CHANNEL IN TELEGRAM TO KEEP UP TO DATE.
















